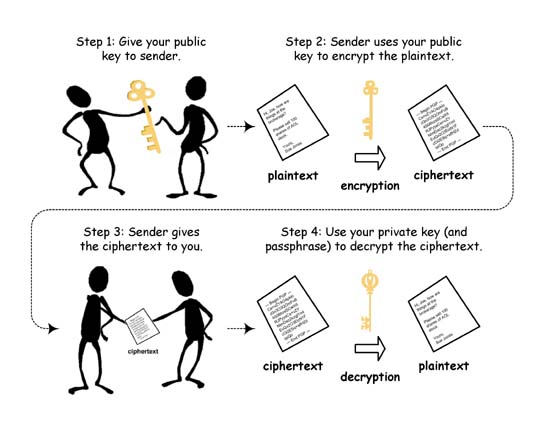
In public key cryptography, the private key is generally kept secret, while the public key may be widely distributed. In a sense, one key “locks” a lock; while the other is required to unlock it. It should not be possible to deduce the private key of a pair given the public key.
There are many forms of public key cryptography, including:
* public key encryption — keeping a message secret from anyone that does not possess a specific private key.
* public key digital signature — allowing anyone to verify that a message was created with a specific private key.
* key agreement — generally, allowing two parties that may not initially share a secret key to agree on one.
Typically, public key techniques are much more computationally intensive than purely symmetric algorithms, but the judicious use of these techniques enables a wide variety of applications. One analogy is that of a locked storefront door with a mail slot. The mail slot is exposed and accessible to the public; its location (the street address) is, in essence, the public key.
Anyone knowing the street address can go to the door and drop a written message through the slot. However, only the person who possesses the matching private key, the store owner, in this case, can open the door and read the message.